100 Series Questions
This TryHackMe Room is a adaptation of the Splunk Boos of the SOC Version 2 event hosted in 2017.
The room is divided into 3 sections with questions of increasing difficulty in each. These are the 100 series, 200 series, and 300 series questions.
TryHackMe has also included additional questions that were not originally part of the event to help with the participants learning.
TryHackMe supplies the dataset and a preconfigure Splunk Search Head.
100 Series Questions:
- Amber Turing was hoping for Frothly to be acquired by a potential competitor which fell through, but visited their website to find contact information for their executive team. What is the website domain that she visited?
The first thing that stands out here is that we should be looking at traffic to a website, meaning that stream:HTTP should eventually be used as a sourcetype in the search query.
The question also gives us a employee’s name, Amber, and that she visited a competitor. Amber is working for a beer company “Frothy”, so we should look for a beer related domain name.
Searching for “Amber” using the index=botsv2 we get the following traffic types.
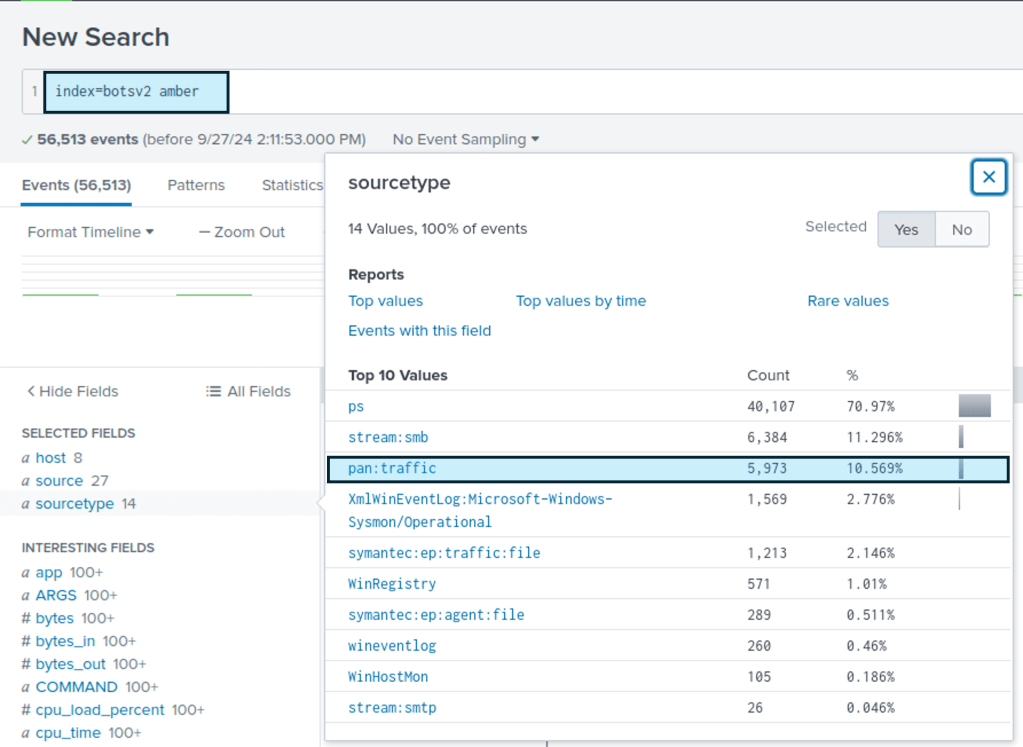
The pan:traffic points to HTTP traffic so that is selected.
Once this is done the src_ip field shows only one ip address which suggests it is Amber’s.
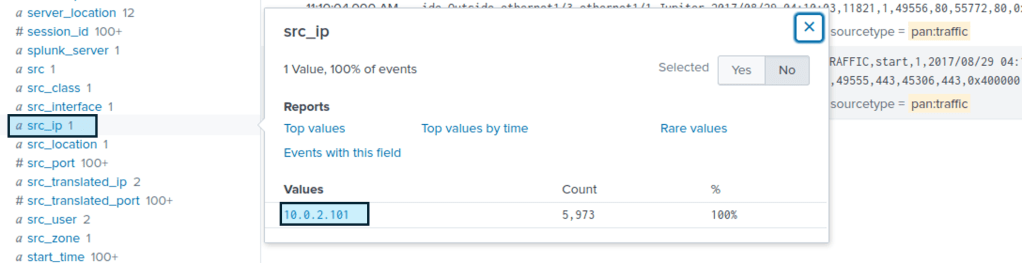
As stated above the sourcetype=stream:HTTP should be used to investigate what websites Amber has visited.
We can also build a table of the websites using the “sites” field provided.
Duplicates will need to be removed for clarity using the “dedup” command.
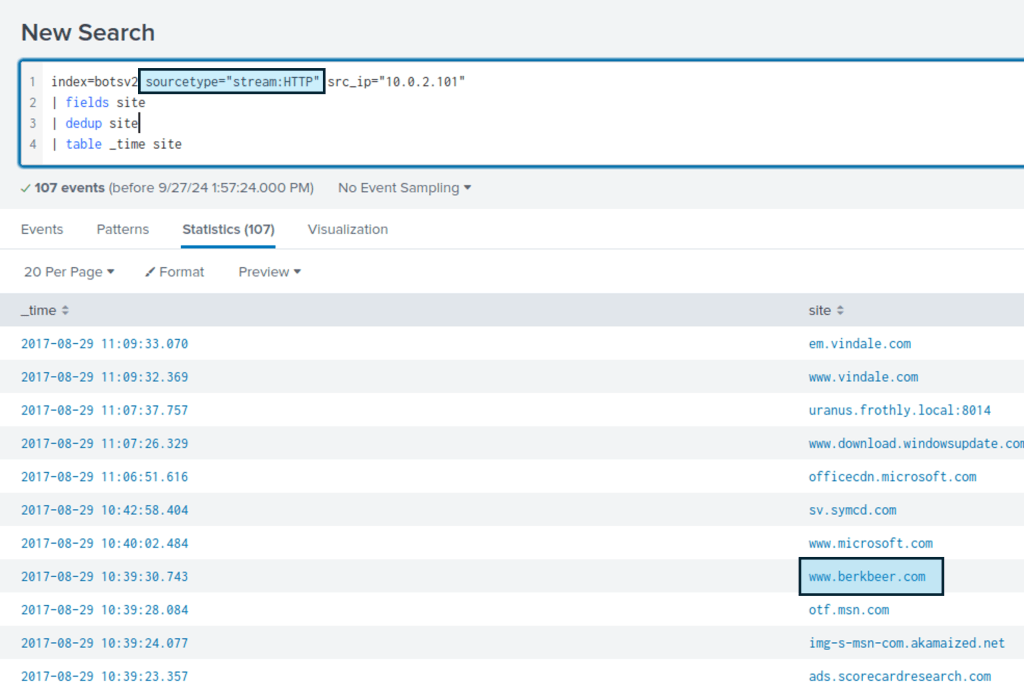
The standout result here is the website “www.berkbeer.com”.
2. Amber found the executive contact information and sent him an email. What image file displayed the executive’s contact information? Answer example: /path/image.ext
So what we now know is that there is a image file that contains the competitors’ CEO contact information.
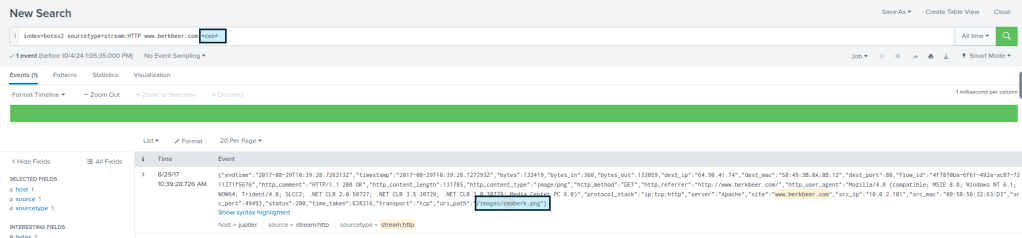
Using the previously found URL “www.berkbeer.com” in the search yields 12 events.
By also inserting the term “*ceo*” we yield a single result.
This shows a uri_path with the pathway “/images/ceoberk.png”
3. What is the CEO’s name? Provide the first and last name.
This requires a change of sourcetype from stream:HTTP to stream:smtp as we are told that Amber corresponded with the CEO via email.
After including this and the keywords “amber” and “berkbeer” the sender email field shows Amber’s employee email.
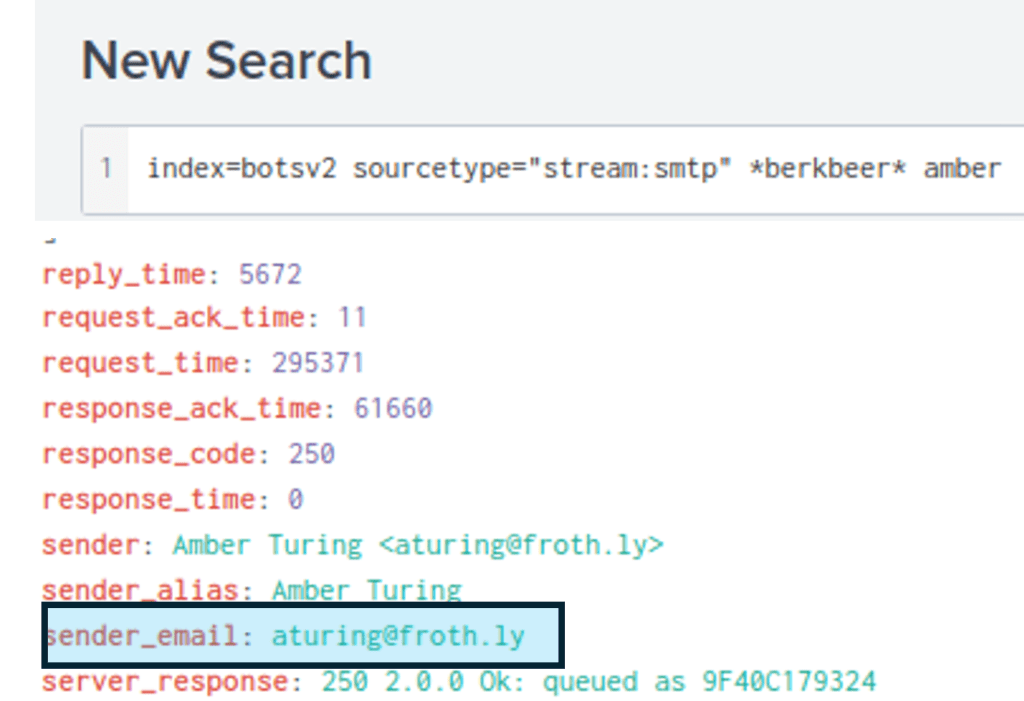
This email address is then entered to the search query (as neither sender or receiver).
After this there is what appears to be a brief email chain between Amber and two Berkbeer email addresses.
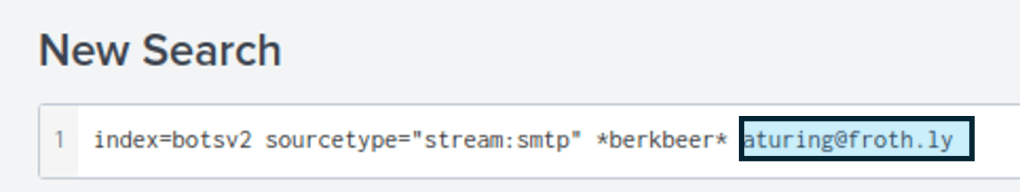
The very first email is sent by Amber to the email address mberk@berkbeer.com

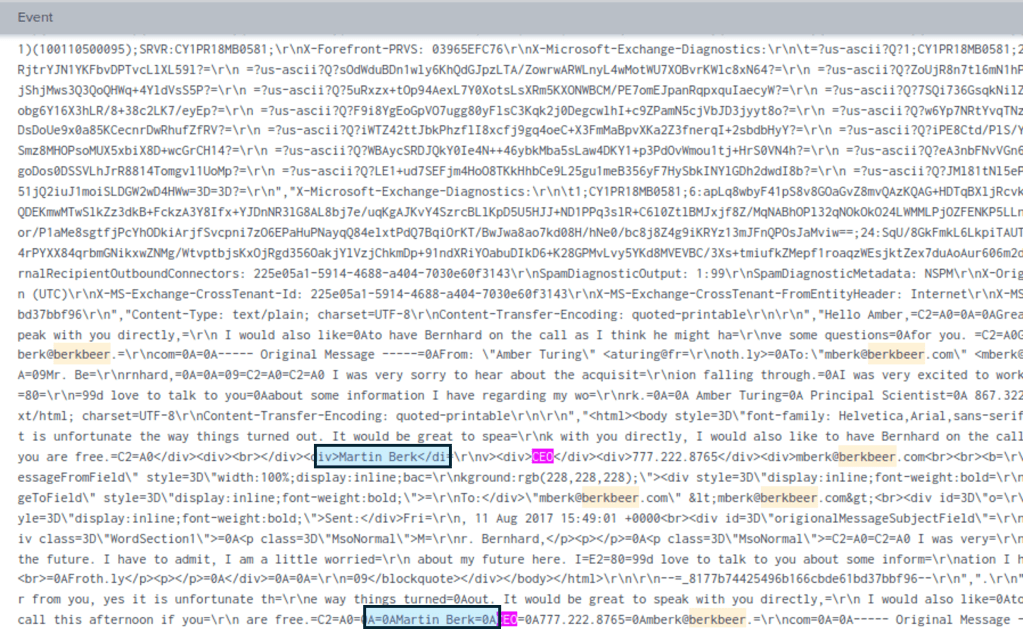
The second email is a response from this email address to Amber.

If we open this event is raw text and the Ctrl + F to search for “ceo” we can see the full name as Martin Berk
4. What is the CEO’s email address?
The answer is already found above.
5. After the initial contact with the CEO, Amber contacted another employee at this competitor. What is that employee’s email address?
As stated above there was a email chain between Amber and two Berkbeer email addresses.
The second email address was hbernhard@berkbeer.com
6. What is the name of the file attachment that Amber sent to a contact at the competitor?
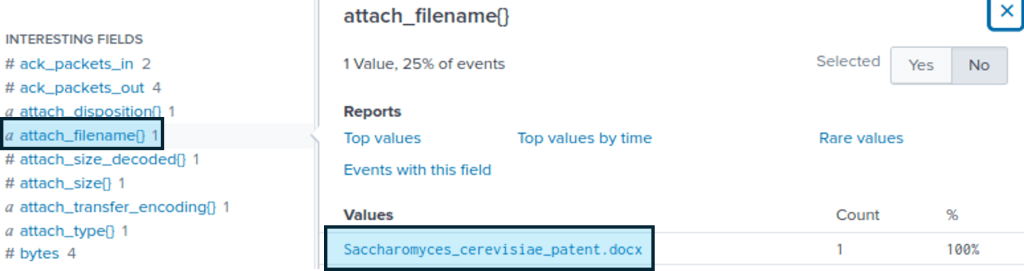
Looking at the interesting fields provided we see a attach_filename listed.
This shows a filename Saccharomyces_cerevisiae_patent.docx
(This is also known as brewer’s yeast)
7. What is Amber’s personal email address?
This is the hardest question in the 100 series.
Rationale would tell us the personal email address must come from Amber herself and if the correspondence is switched from a business email to personal it should be the final message in the chain.
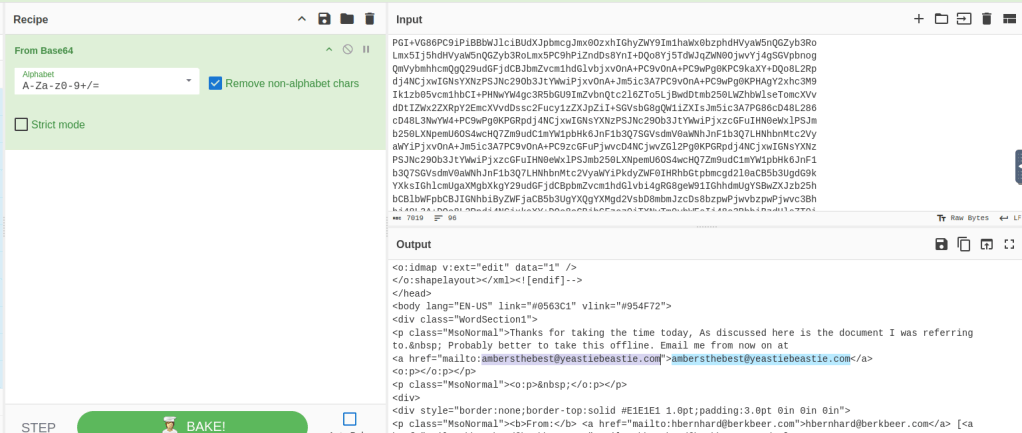
Uisng the hint provided we are looking for encoded messages.
By looking at the final email there is a content section that looks encoded

A later section shows the content is encoded using base64.

Decoding this we find Amber’s personal email address



Leave a comment